SMEC Ethical Hacking Training

SMEC Ethical Hacking Training
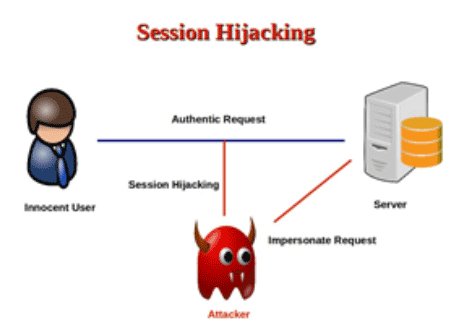
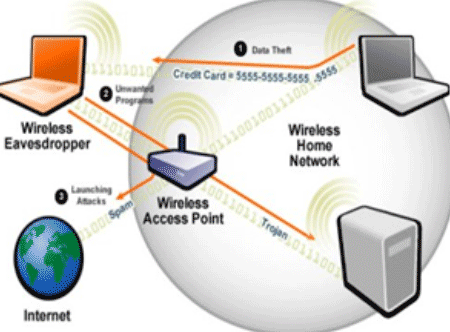
A SMEC Ethical Hacker is a skilled professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). The SEH credential certifies individuals in the specific network security discipline of Ethical Hacking from a vendor-neutral perspective.